You are configuring captive portal on your SRX Series device for guest user access.When would you use the redirect-traffic all command?()
第1题:
A. syn-fin, syn-flood, and tcp-no-frag
B. syn-fin, port-scan, and tcp-no-flag
C. syn-fin, fin-no-ack, and tcp-no-frag
D. syn-fin, syn-ack-ack-proxy, and tcp-no-frag
第2题:
You are configuring a Cisco multilayer switch for the Company network. Which command would you use to configure a port to act as a routed interface?()
第3题:
You are the administrator of Ezonexam.com's network.
You want to connect your Windows 2000 Professional computer to a new TCP/IP based laser print device. The print device is Plug and Play compliant and is included on the current Hardware Compatibility List (HCL). When you attempt to create a new TCP/IP printer port you receive the following error message:
"Specified Port cannot be added. The port already exists."
You want to be able to use the new TCP/IP printer.
What should you do?
A.Modify the properties of the existing printer port to use the new print device.
B.Change the LPT port setting to bidirectional in the BIOS on your computer.
C.Change the LPT port setting to enable legacy Plug and Play detection on your computer.
D.Obtain and install the WDM-compliant device drivers and printing software for the printer.
第4题:
You work as the exchange administrator at Company.com.the Company.com network contains an exchange server 2010 organization.Company.com has its headquarters in stockholm where you are located.you are responsible for an exchange 2010 edge transport server named -ex01.during the course of the week you receive an instruction from the cio to make sure that e-mail messages sent to unknown addresses in the organization is rejected automatically.What should you do?()
第5题:
When configuring port security on a Cisco Catalyst switch port, what is the default action taken by the switch if a violation occurs? ()
第6题:
You configure your Windows 2000 Professional computer for Internet Connection Sharing and for TCP/IP filtering as shown in the exhibit.
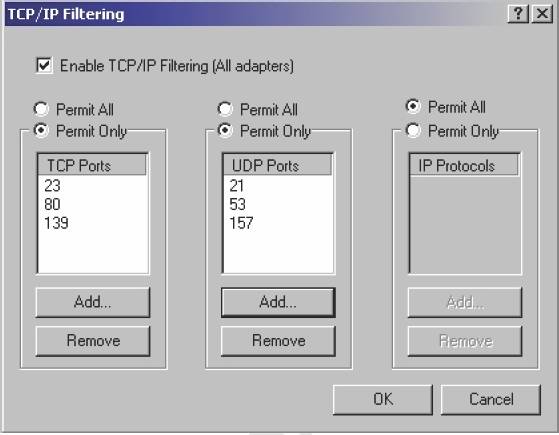
You test your TCP/IP filtering configuration from another client computer. You can access web sites, but you cannot access FTP sites.
What should you do to be able to access FTP sites?
A.Add Port 21 to the TCP Ports section.
B.Add Port 138 to the TCP Ports section.
C.Add Port 21 to the IP Ports section.
D.Add Port 138 to the IP Ports section.
第7题:
You are configuring an 802.1Q trunk between a Layer 2 switch and a firewall. You read in the documentation that the best way to set up a trunk is to set the port as dynamic desirable. The trunk is not coming up. Which one of these options would be a valid explanation? ()
第8题:
A. When you want all unauthenticated traffic to be redirected
B. When you want all clear text traffic to be redirected.
C. When you want all authenticated traffic to be redirected.
D. When you want all encrypted traffic to be redirected.
第9题:
When configuring unified ports on a 5548 switch, which port ordering must be respected?()
第10题:
You install a third-party application on your computer. The application uses port 80 to negotiate a listening port. After establishing the listening port, the application uses dynamic ports above 6000. You need to configure Microsoft Windows Firewall to allow traffic for the application. What should you do? ()